All- in – one fully encrypted communications APP
+ HF Radio with LRDR to overcome congested,
compromised and contested communications.
C2/VoIP/Chat/Web Search Engine

GAME CHANGING
COMMUNICATIONS, SECURITY
AND PRIVACY
ShieldCom is the solution for secure personal communications and transmission services. A fully encrypted system raises the standards from 256-bit encryption to “post quantum” standards well suited for areas of conflict, natural disasters and emergency situations. Combined with HF radio and LRDR it makes our communications system formidable no matter the situation.
You can choose as many people or departments as you want to be in your communications network. Now users can get in touch with loved ones even in the worst conditions safely.
ShieldCom is the go-to-app recognized as a life saving resource when communications need to be available and protected.
LOCK OUT HACKING, SCANNING AND TRACKING.
COMMUNICATE ANYWHERE WITH CONFIDENCE.
Simple easy-to-use interface masks the latest in high-level security technology.
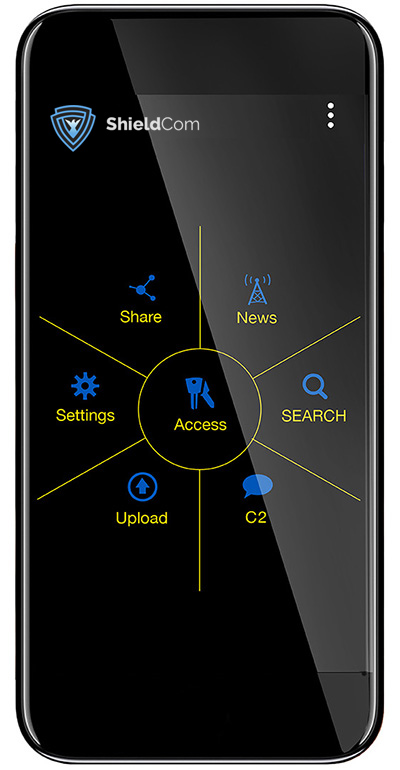
HOME SCREEN
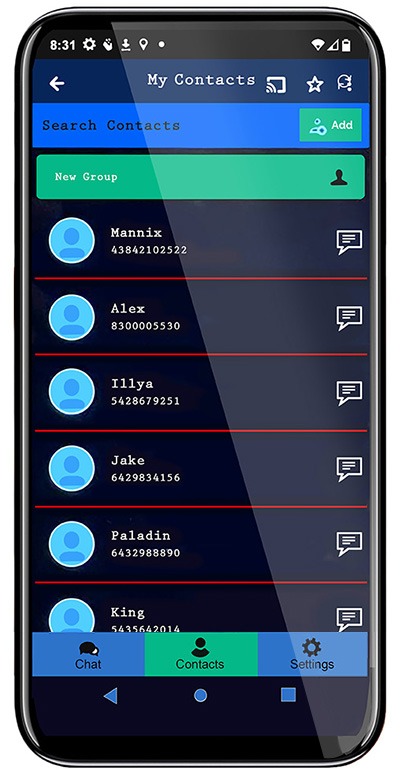
CONTACTS
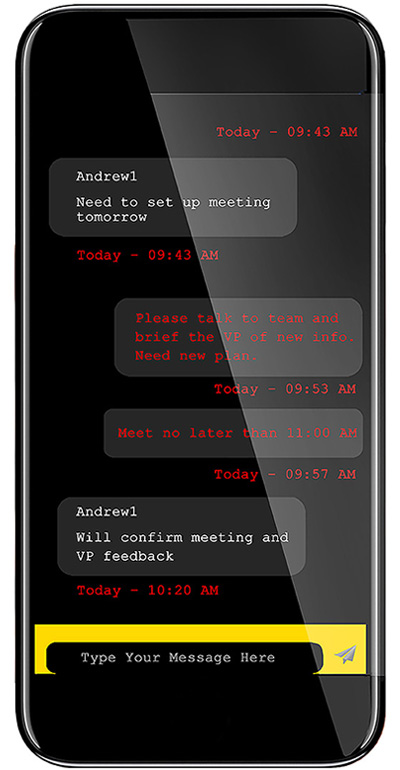
CHAT
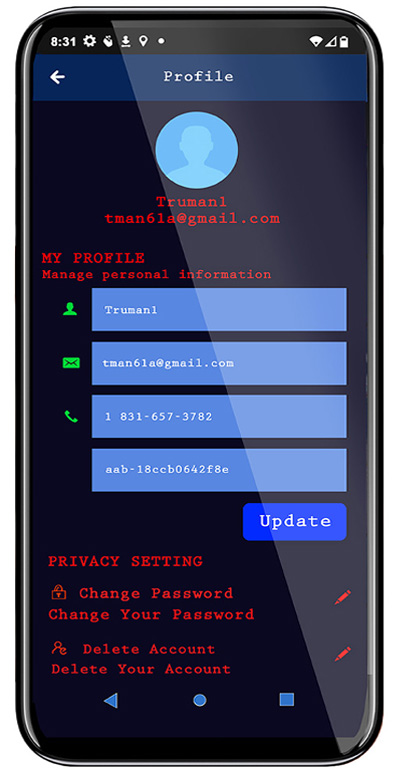
PROFILE INPUT

WEB SEARCH RESULTS

VIDEO
(not available in HF radio)

SHIELDCOM NETWORK
TO DEPLOY FORTRESS
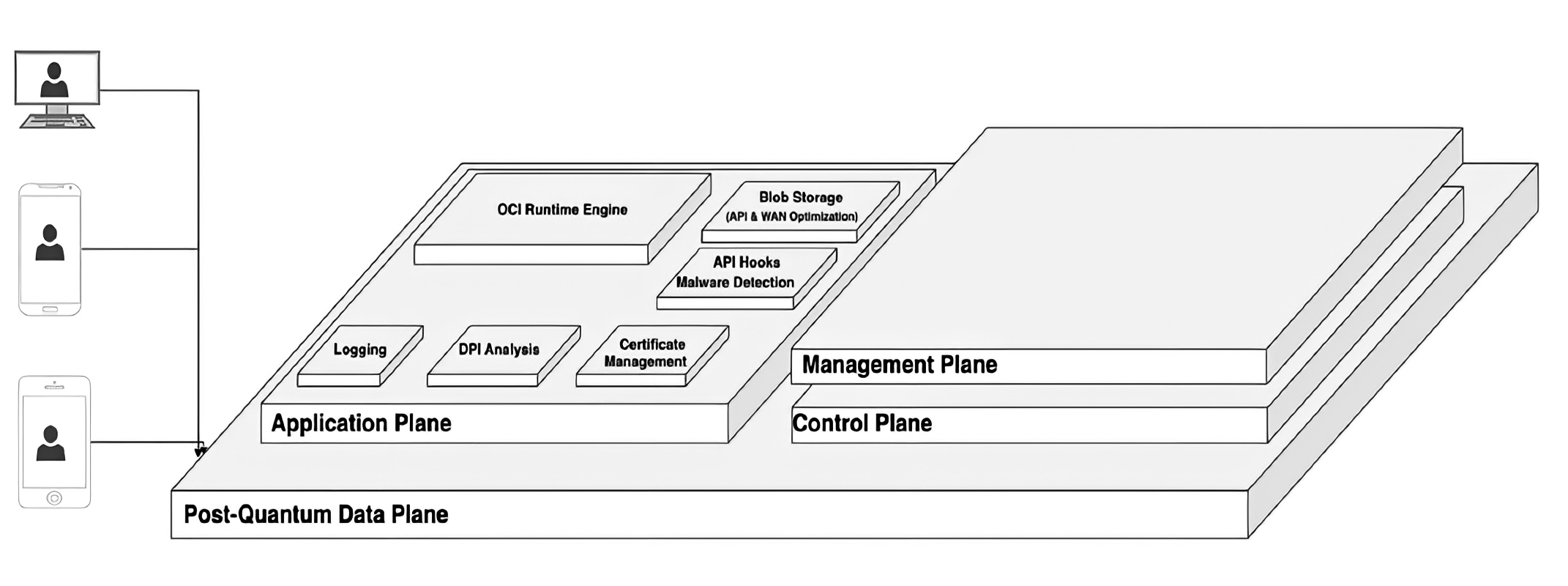
ShieldCom is partnering with American Binary, a cutting edge military grade encryption network.
Fortress™ is a Quantum Safe Software Defined Network designed to address the need to simplify the transport layer of distributed enterprise networking from data center, to cloud, to endpoint, to edge. This allows deployment of a globally connected network of resources almost instantly.
All of this is independent of routing protocols, traditional IPsec tunnels, IP address schemas, and security policies.
UNPRECEDENTED CIVILIAN SECURITY AND
COMMUNICATIONS FOR THE LONG TERM
POST
QUANTUM
CRYPTOGRAPHY
• Centrally monitored
• Managed, and controlled with ease
• Supporting 10K+ nodes
• All communicating on a highly encrypted, incredibly fast transport layer.
• Utilizes state-of-the-art extended shelf-life cryptography good for the next 30 years
• The cryptography used is also referred to as
post-quantum
• Leverage already owned assets to participate
in the deployment, management, logging, and
monitoring of the product.
